views
A proof-of-concept exploit code has surfaced online for a Windows flaw, which could allow attackers to infiltrate full networks of companies by gaining administrative powers. As a result, attackers exploiting this breach in the Windows source code can get access to a company’s domain controllers, hence bypassing any authentication standard and getting access to highly sensitive data that enterprises may have within their own networks. Due to its nature of filling authentication fields with zeros, the Windows flaw has been named ‘Zerologon’, and is essentially a privilege escalation glitch. With a CVSS impact score of 10 out of 10 according to Tenable, it is also a top priority breach that can essentially pose a serious threat to enterprises using Windows PCs at work.
The flaw has already been addressed by Microsoft in its August 2020 security patch. However, according to a report in ThreatPost, at least four public proof-of-concept exploits for Zerologon were released on Github this week. Researchers working with Secura discovered the flaw, and have published the technical details of the flaw for the security community to inspect.
The researchers said that the breach allows an attacker latched on to a company’s local network to completely compromise the Windows domain of the respective company. The breach completely bypasses authentication, which helps attackers escalate their system privileges on a breached PC. According to reports, the flaw stems from the Netlogon Remote Protocol, which is available on Windows domain controllers that are used for tasks such as user and machine authentication – key features for enterprise security. It also exists in the AES-CFB8 encryption setup for Netlogon sessions.
In these sessions, the encryption standard randomises the system login initialisation process, which makes it practically impossible for attackers to breach enterprise systems. However, the Netlogon flaw fails to randomise the initialisation, and instead sticks to a 16-bit vector for a single login attempt. This, in turn, gives attackers easier control over gaining access to a system.
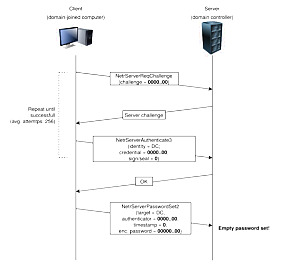
Security researchers at Secura said that due to incorrect use of an AES encryption process, it is possible for attackers to clone user identities and subsequently set empty passwords, further escalating the breach. However, it is important to note that in order to exploit the vulnerability, the attacker will have to launch the attack from a machine on the same local network. This means that they would need physical presence within the targeted network, such as access to a Windows PC within an enterprise network.
As for its effects and the impact, attackers can choose to breach private files within an organisation and hence become privy to sensitive financial documents, and also use access to a system to inject ransomware into enterprise networks. Given that the exploits have been published on Github, all enterprises are being urged to install Microsoft’s newest system security patch right away. Microsoft is also addressing the issue in two phases – the first with a voluntary update last month, and the second being a ‘forced’ update to roll out in 2021.


















Comments
0 comment