views
Analyzing the Attack
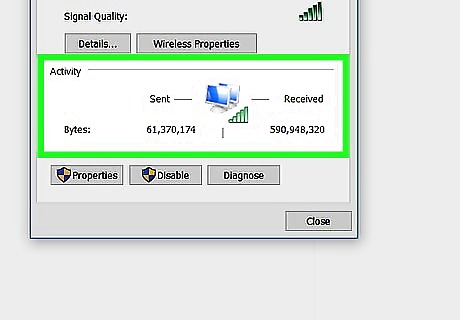
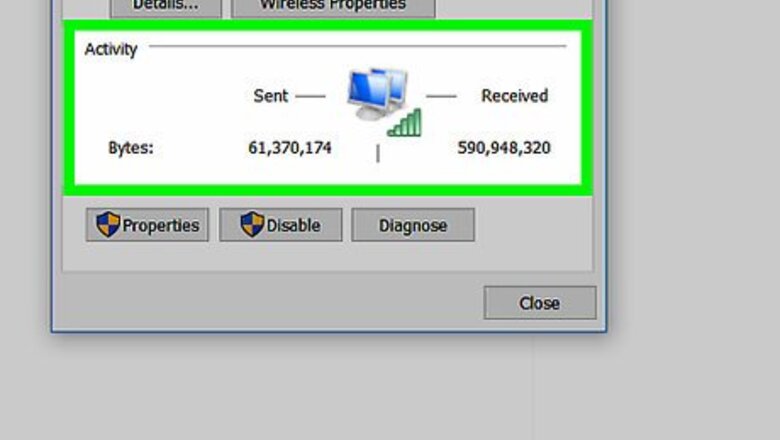
Monitor your network traffic. When you make the report, you may be asked about specifics of the attack. It is useful if you have this information already on hand. Look over your website’s analytics, logs, graphs, and traffic. Gather as much information as is available to you. If you use a webhost, such as Wordpress, the host will usually provide some website analytics for you through their online portal. Contacting the web host directly may also help you find this information. If you host your own web servers and use a website monitoring service, such as Loggly or Wireshark, use their software to identify patterns in your traffic. If you do not have a monitoring program set up already, you may not be able to access this data without using advanced commands. Try contacting your internet provider.
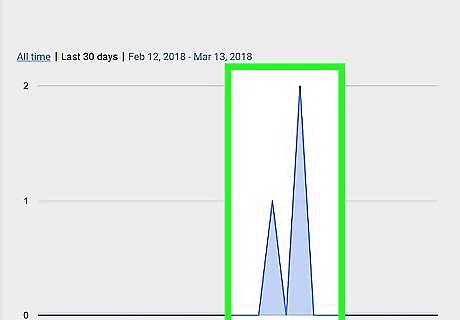
Determine when the attack began and ended. Using graphs or analytic data, look at when the spike in traffic first began. This will indicate when the attack began. If the attack is over, check to see when the traffic has dropped. If the attack is ongoing, make a note of how long it has lasted. Ask yourself, is this attack coinciding with another event? For example, if you just launched a new program or if your company was in the news recently, consider if you could have been targeted.
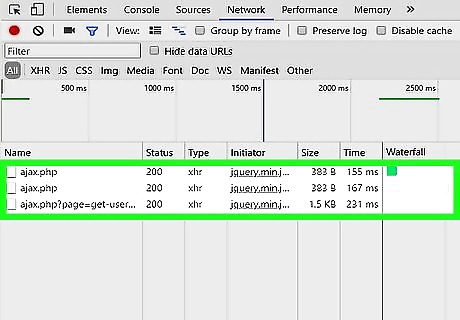
Identify the type of traffic flooding your website. Look at the packets in your network logs. There are various types of packets, such as SYN packets, ping packets, or UDP packets. An abnormal increase in any 1 type can be the cause of your DDoS attack. Your web logs or traffic tracker will usually allow you to check each type individually. If your site or server has been overwhelmed with SYN (or synchronized) packets, you likely have a Transmission Control Protocol (TCP) flood. If you were overwhelmed by ping packets, you may have an Internet Control Message Protocol (ICMP) flood. If you have been overwhelmed with User Datagram Protocol (UDP) packets or Domain Name System (DNS) queries, you may have a UDP flood. You don't need to know what these packets are doing. You just need to identify what type is flooding your system so that your internet provider or host can reduce the flood. If you can't identify the type of traffic, don't worry. There are many different types of DDoS attack. Your provider may be able to help you when you report the attack.
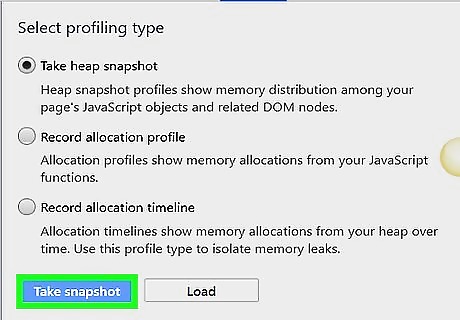
Make copies of any communication sent to you by the attackers. Sometimes, DDoS attacks are an attempt to blackmail or threaten a company or site owner. In these cases, you may receive messages demanding payment or asking you to take down content. Always save any messages from attackers. If you were asked to make a crypto currency payment, save the information that the attacker gives you, including their wallet address, transaction receipts, email address, and type of currency used. Print off emails and store them in a safe place. Forward them to another safe address as well.
Contacting Your Provider
Contact your web hosting service if you do not host your own website. If you use a web hosting service, such as WordPress or GoDaddy, report your DDoS attack to them. Use live web chat or a phone to contact your web host. An email may not be answered in time to help. Sometimes, web hosting services come under DDoS attacks themselves, which can affect every website they host. If this is the case, your hosting service should notify you. They will handle the DDoS attack from there.
Call your internet provider if you do host your own web servers. If you do not use a hosting service and have your own web servers, call your internet provider, such as Time Warner, Comcast, or Virgin. Ask to speak to an operations specialist about a DDoS attack on your servers. Many internet providers have emergency numbers listed on their website for situations like this. Call these numbers for immediate help.
Explain that you are currently the victim of a DDoS attack. If possible, tell them what type of protocol is overwhelming your system. If you cannot identify the source of the attack or protocol used, your provider can try to identify it for you. Provide as much detailed information as possible. Provide any information about packet sizes, types of protocols used, or the source of IP addresses to help the investigators.
Follow the provider’s instructions to mitigate the attack. Mitigation is the process of stopping or reducing the damage of the attack. Your provider may give you instructions on how to block certain types of traffic. They may inform other providers about the attack to reroute some of the traffic. Your internet provider may recommend scaling up your website. This means that they will increase your bandwidth to protect against future attacks.
Filing a Police Report
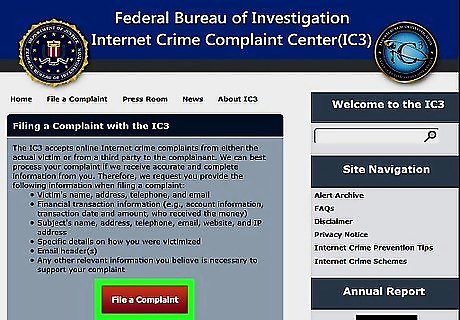
File a report with law enforcement if you lost money in the attack. You can report a DDos attack to law enforcement if you were threatened or blackmailed or if you lost money as a result of the attack. In most cases, contact your national web crime unit. In the US, file a complaint online with the FBI’s internet crime complaint center here: https://www.ic3.gov/default.aspx. In the UK, call 0300 123 2040 to report the attack to the National Fraud and Cyber Crime Reporting Centre. In Australia, submit an online report to the Cyber Security Center. In Canada, contact your local police department.
Provide information about the attack. To investigate, police will need as much as information about the attack as possible. Tell them what you can about the attack. Be sure to include: When the attack started and ended. If the attackers asked for a ransom and whether you paid it. If you were threatened before the attack. What protocols (UDP/DNS, TCP, or ICMP) were used in the attack. Any unusual patterns or observations during the attack.
Explain why you think you were attacked. If you suspect there was a reason behind the attack, be sure to explain why in your report. If you were threatened beforehand or if the attackers asked for money, always include this information. Other reasons behind attacks might include: You published something with a different ideology than the attacker. You have a competitor or rival. The attack was a distraction to try to steal data from your website or company.
Include any correspondence you had with the attackers. If the attackers asked for ransom, threatened you, or sent any message to you, copy the text of these messages. Either upload a copy of the original message or copy and paste the message into your report. If you already paid a ransom to the attackers, give the investigators the attacker’s crypto currency wallet address or email address. If the agency decides to pursue a case against the attackers, you may be asked for hard copies of your evidence, including emails, payment transactions, or screenshots of the attack. Keep the original copies in a safe place.
Discuss how the attack affected your business or website. To encourage law enforcement to investigate the issue, be sure to state any financial impact this attack may have had on your business. If you lost customers, money, or data during the attack, tell them. State how you earn income from the website. For example, you might sell products, offer online services, or earn money through advertising. Try to come up with estimate of your total losses, based on how much money you typically make in an hour or day from your site. Report any customer or user complaints to help emphasize how the attack affected your network.
Wait for a response from the investigators. In a few weeks, you should receive an email regarding your complaint. DDoS attacks can be difficult to prosecute. Unless the government has a strong lead on your attacker, they may not be able to follow up on your complaint. If law enforcement decides to investigate and prosecute your attackers, you may be asked to supply copies of evidence, such as emails or screenshots of the attack. If they have not decided to investigate at this time, they will notify you. You may be asked to keep your documents in a safe place, just in case they decide to prosecute in the future.

















Comments
0 comment