views
Creating the CSRF Class File
Create csrf.class.php. This is the file that will contain all the functions in that will be used to prevent CSRF attacks.
Save the file. All of the code in Parts 2 and 3 will be added to the end of this file.
Adding a Random Token
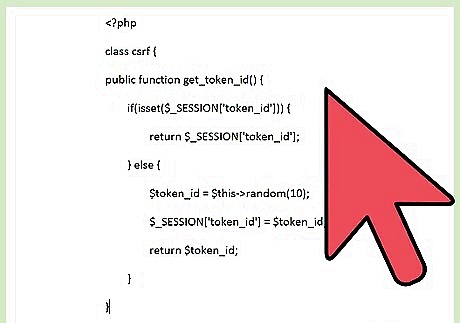
Create the get_token_id() function. This function retrieves the token ID from a user's session, and if one has not already been created generates a random token. public function get_token_id() { if(isset($_SESSION['token_id'])) { return $_SESSION['token_id']; } else { $token_id = $this->random(10); $_SESSION['token_id'] = $token_id; return $token_id; } }
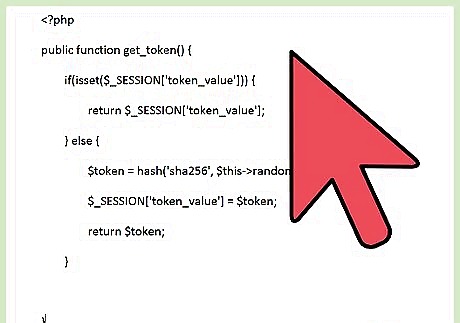
Create the get_token() function. This function retrieves the token value, or if one has not been generated, generates a token value. public function get_token() { if(isset($_SESSION['token_value'])) { return $_SESSION['token_value']; } else { $token = hash('sha256', $this->random(500)); $_SESSION['token_value'] = $token; return $token; } }
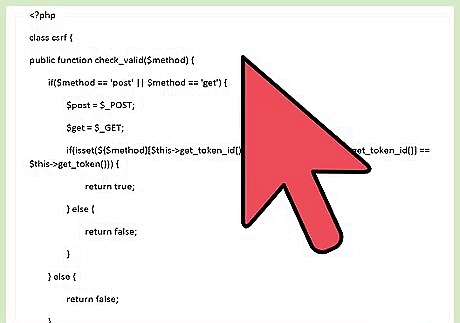
Create the check_valid() function. This function determines whether the token ID and the token value are both valid. This is done by checking the values of the GET or POST request against the values stored in the user's SESSION variable. public function check_valid($method) { if($method == 'post' || $method == 'get') { $post = $_POST; $get = $_GET; if(isset(${$method}[$this->get_token_id()]) && (${$method}[$this->get_token_id()] == $this->get_token())) { return true; } else { return false; } } else { return false; } }
Generating a Random Name for Each Form Field
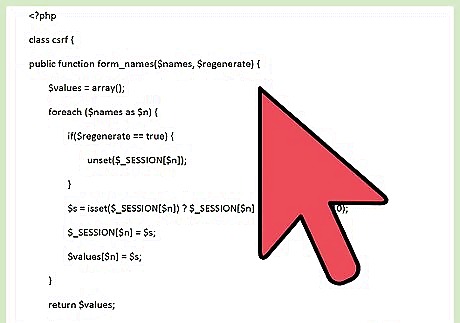
Create the form_names() function. This function generates random names for the form fields. public function form_names($names, $regenerate) { $values = array(); foreach ($names as $n) { if($regenerate == true) { unset($_SESSION[$n]); } $s = isset($_SESSION[$n]) ? $_SESSION[$n] : $this->random(10); $_SESSION[$n] = $s; $values[$n] = $s; } return $values; }
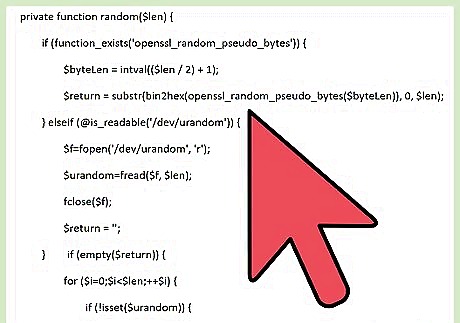
Create the random function. This function generates a random string using the Linux random file to create more entropy. private function random($len) { if (function_exists('openssl_random_pseudo_bytes')) { $byteLen = intval(($len / 2) + 1); $return = substr(bin2hex(openssl_random_pseudo_bytes($byteLen)), 0, $len); } elseif (@is_readable('/dev/urandom')) { $f=fopen('/dev/urandom', 'r'); $urandom=fread($f, $len); fclose($f); $return = ''; } if (empty($return)) { for ($i=0;$i<$len;++$i) { if (!isset($urandom)) { if ($i%2==0) { mt_srand(time()%2147 * 1000000 + (double)microtime() * 1000000); } $rand=48+mt_rand()%64; } else { $rand=48+ord($urandom[$i])%64; } if ($rand>57) $rand+=7; if ($rand>90) $rand+=6; if ($rand==123) $rand=52; if ($rand==124) $rand=53; $return.=chr($rand); } } return $return; }
Close the class csrf bracket. }
Close the csrf.class.php file.













Comments
0 comment